1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
| var targets = []
Thread.sleep(1)
while (targets.length == 0){
targets = Process.enumerateModules().filter(mod => mod.name.indexOf("lua") != -1)
send("find lua lib , wait ...")
}
send(targets)
function run(targets) {
targets.forEach((target)=>{
console.log(target.findExportByName('luaL_loadstring'))
var luaL_newstate = new NativeFunction(target.findExportByName('luaL_newstate'),'pointer',[]);
var lua_pcallk = new NativeFunction(target.findExportByName('lua_pcallk'),'int',['pointer','int','int','int','int','int'])
var luaL_loadstring = new NativeFunction(target.findExportByName("luaL_loadstring"),'int',['pointer','pointer'])
var lua_tolstring = new NativeFunction(target.findExportByName("lua_tolstring"),'pointer',['pointer','int'])
var luaL_openlibs = new NativeFunction(target.findExportByName('luaL_openlibs'),'void',['pointer']);
var lua_State = luaL_newstate();
console.log("luaL_openlibs:"+luaL_openlibs(lua_State))
var scr= 'function enco()\n' +
' -- ...略\n' +
' print("mytest")\n' +
'\tprint(type(print)) \n' +
'\ttab1 = { key1 = "val1", key2 = "val2", "val3" }\n' +
'\tfor k, v in pairs(tab1) do\n' +
'\t\tprint(k .. " - " .. v)\n' +
'\tend\n' +
'\tc = 5 -- 全局变量\n' +
' local d = 6 \n' +
'\ta = 21\n' +
'\tb = 10\n' +
'\tq = a + b\n' +
'\tlocal myArray = {10, 20, 30, 40, 50}\n' +
'\tarray = {}\n' +
'\tfor i=1,3 do\n' +
'\t array[i] = {}\n' +
'\t\t for j=1,3 do\n' +
'\t\t\t array[i][j] = i*j\n' +
'\t\t end\n' +
'\tend\n' +
'end\n' +
'local data = string.dump(enco)\n' +
'local fp = io.open("data/data/cc.chenhe.lib.androidlua.demo/enco.luac","w")\n' +
'fp:write(data)\n' +
'fp:close()\n'
var luaL_loadstring_ret = luaL_loadstring(lua_State,Memory.allocUtf8String(scr))
console.log("luaL_loadstring_ret : "+luaL_loadstring_ret)
if(luaL_loadstring_ret == 0)
console.log("load lua ini t ret "+ lua_pcallk(lua_State,0,-1,0,0,0) + " str :"+lua_tolstring(lua_State, -1).readCString())
})
}
console.log(targets[0].name)
run(targets)
|
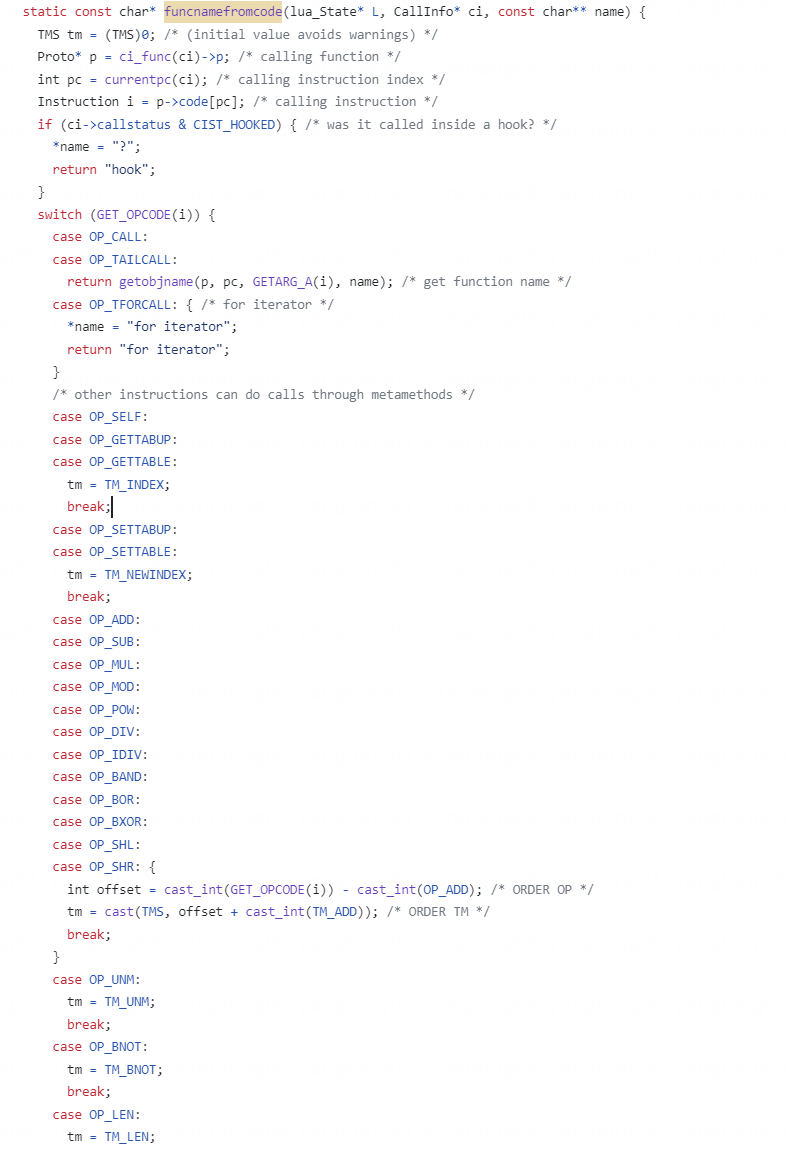
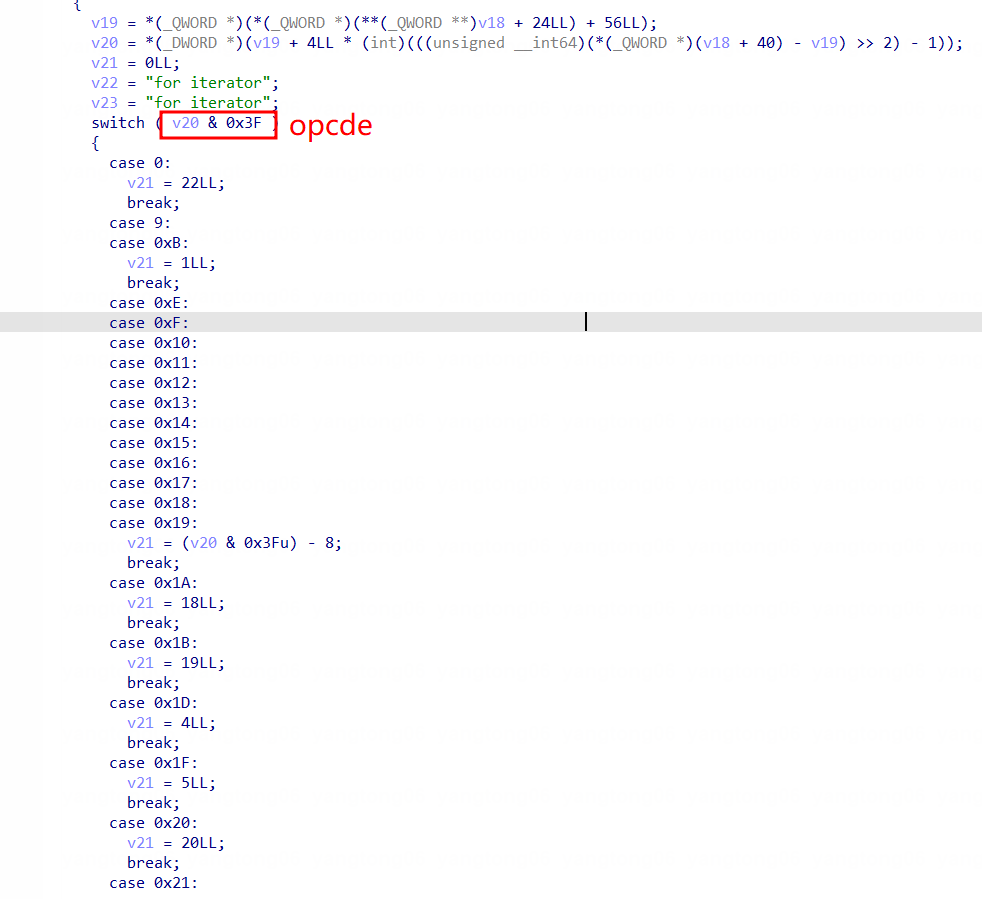
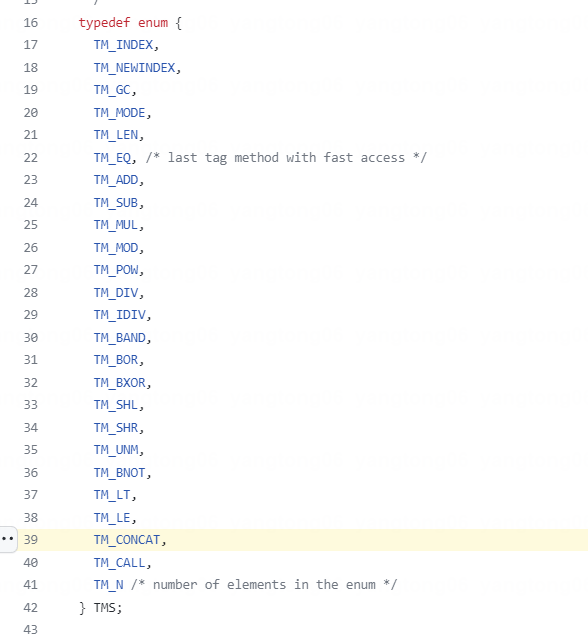
 除了众所周知的luaV_execute以外,还可以通过其他地方比如funcnamefromcode进行分析。
除了众所周知的luaV_execute以外,还可以通过其他地方比如funcnamefromcode进行分析。